Maybe you think that e-mails are only plain text based messages but the source code hides a lt of technical information. Accessing the source code may be useful to discover certain data such as authenticity of the sender, servers it has gone through and phishing attempts.
The information is extremely useful when you try to detect any kind of fraud or possible threat to your digital security. In fact, some hackers try to replace the identity of the sender or official organisms through false mail accounts. Thanks to the source code verification you can check if it’s legit or a scam. E-mails source code is vital information for your own security.
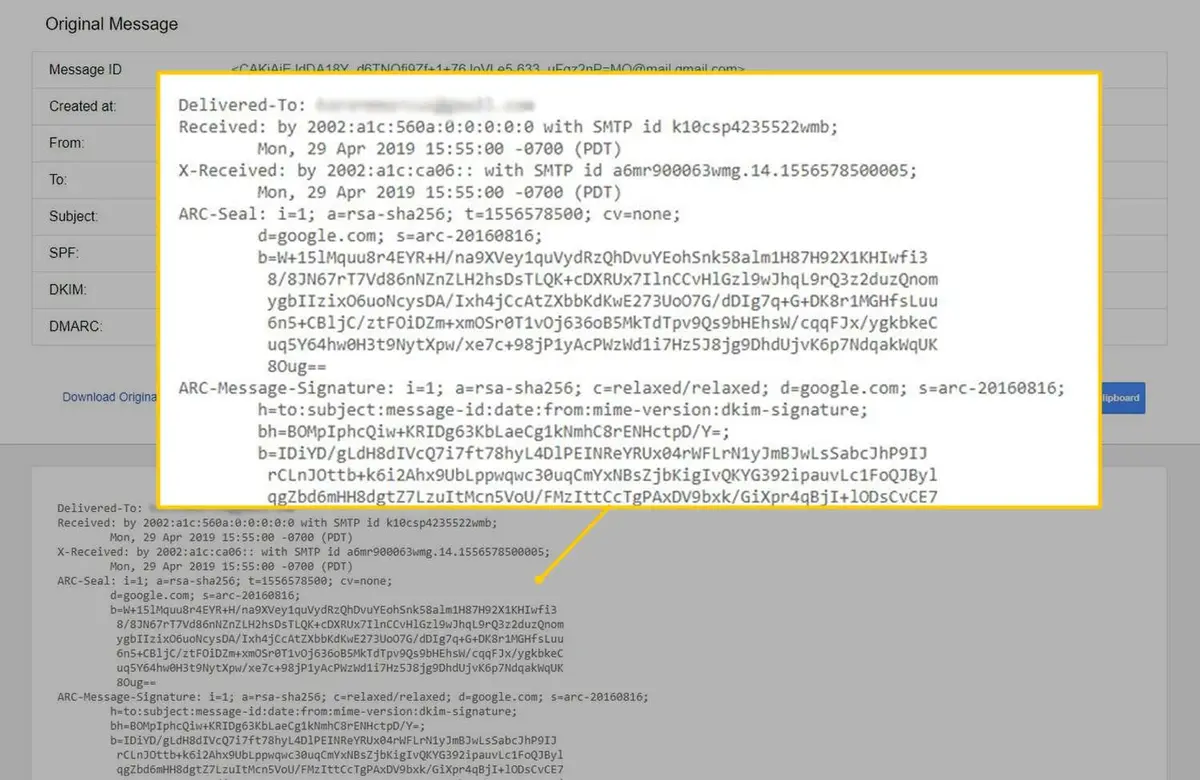
Ways to see the source code of your e-mails
There’s a lot of hidden information in e-mails source code. It’s data that does not appear on the body of the mail but you can easily open it with a little knowledge. You will find information such as IP addresses, mail headers and authentication protocols, for example. In case you analyze this information you can detect any kind of phishing attempt, as well as the origin of the message or if the communication has been altered.
Depending on each e-mail service, the methods to access the source code can vary. The two most popular ones are Gmail and Outlook.
Check source code in e-mails through Gmail
Open your Gmail account using the web browser and open any e-mail from your inbox. Click the three dots button to access options menu and select Show original. Then you will see a code format text with the information from the source code.
Check e-mails source code in Outlook
The Microsoft Outlook platform also shows you the source code of any e-mail. You just need to select the e-mail you want to review and click on the three vertical lines button. There click on the View message origin and you will have access to the source code.
Which information can you extract from the source code?
When you are in front of the text from the source code, you can check different sections to highlight authentic data or suspicious information. For example, extract sensible information such as:
- IP address of the original server to see if it coincides with the company. Search on the network and see if it’s the same of the e-mail.
- DKIM, SPF and DMARC headers. These indicate if the message comes from the real domain of the sender.
- Server tracking. In case you see any suspicious server that the message has gone through, you can already report it for security reasons.
- Hidden links and possible redirection. The source code can provide you a detail of strange links hidden along the mail.
This is the information you can learn to revise in e-mails source code. It’s a great tool to improve your security and defense on the Internet.

