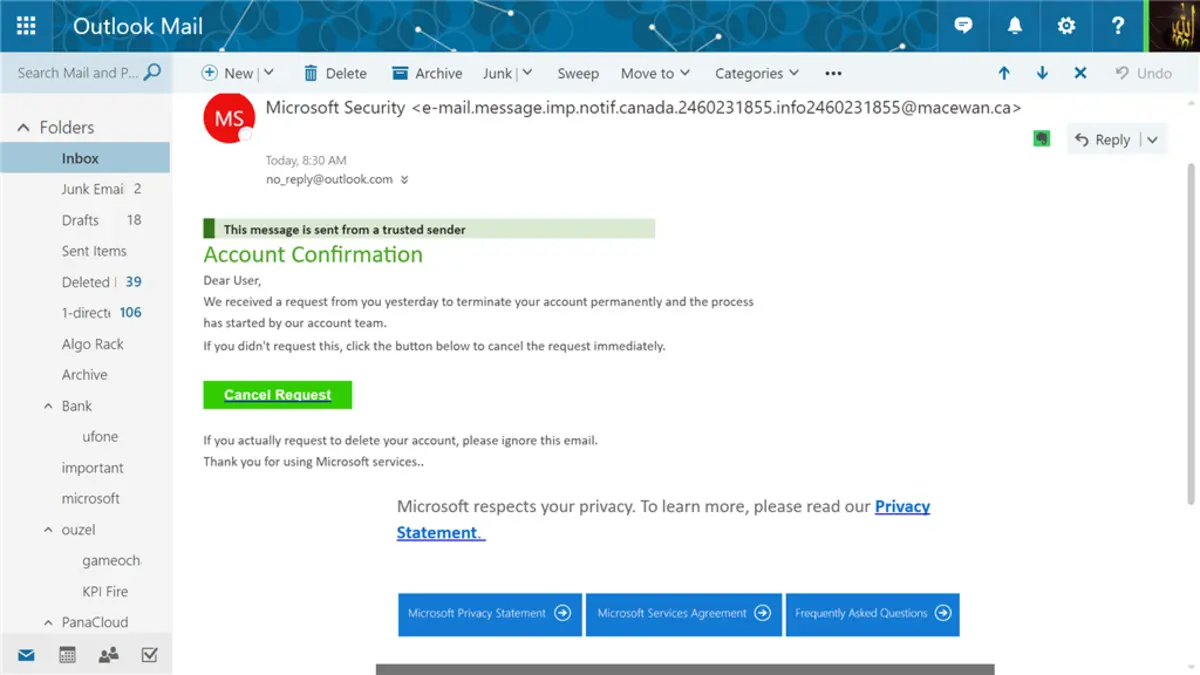
There are different methods to try hacking your e-mail. The most popular one is called Phishing. It consists on a false link to log in and then the hacker steals your password. Another possibility is the use of Trojans, viruses or even brute force to try hacking an e-mail with a poor password.
In case your e-mail is victim of a hacking intent, there are some steps you can take as prevention. This article covers the most effective ones in order to recover the control, security and privacy of your electronic mail account. There’s also a difference between a hacking intent on your e-mail to lose control over it, but there are actions to take in each case.
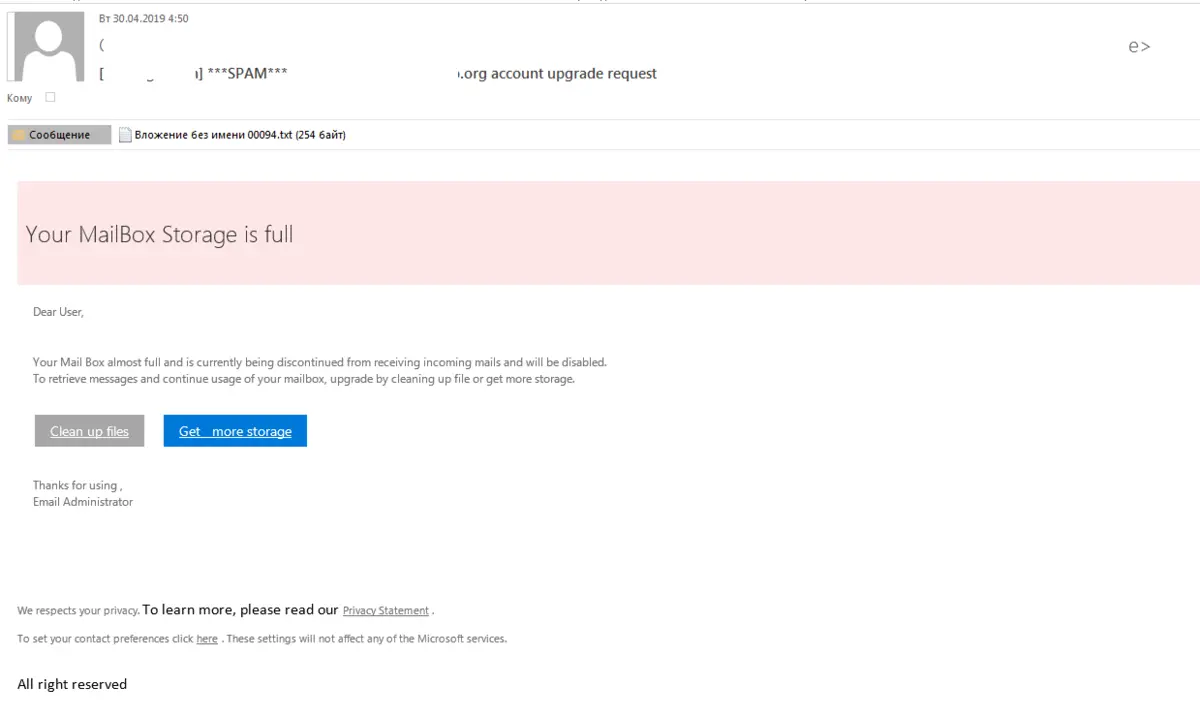
Hacking intent on your e-mail and what to do after it
These actions should be taken in case of a hacking intent on your e-mail account as well as other social media or apps. If you are quick enough you can prevent new attacks and recover the security barriers for your services.
Change the password
First you must change your password in case someone has been trying to log in without your permission. In case you already know that your e-mail was compromised, the best decision is to create a new key. Try choosing a secure password to make it even harder to breach in the future.
Use the recovery options
If your account has been stolen you have some alternatives to try recovering control over it. Indicate that you forgot the password and complete the personal information to receive new access and create a new password.
Talk with your contacts
Don’t waste any time and talk with friends and family. Tell them that your account has been hacked and to ignore any mail using your name at least for a while. Hackers tend to use stolen e-mails to try luring new victims to their scams.
Check your device
It’s important to check your own device if a hacking intent on your e-mail occurred. Sometimes you install a virus or there’s a system vulnerability that weakens the defenses. The programs and operative system should also be updated to prevent any attack.
By following these indications you should easily protect your computer and e-mail account from hacking activities. It’s easy to do and very quick.

Do you have any questions or problems related to the topic of the article? We want to help you.
Leave a comment with your problem or question. We read and respond to all comments, although sometimes it may take a while due to the volume we receive. Additionally, if your question inspires the writing of an article, we will notify you by email when we publish it.
*We moderate comments to avoid spam.
Thank you for enrich our community with your participation!