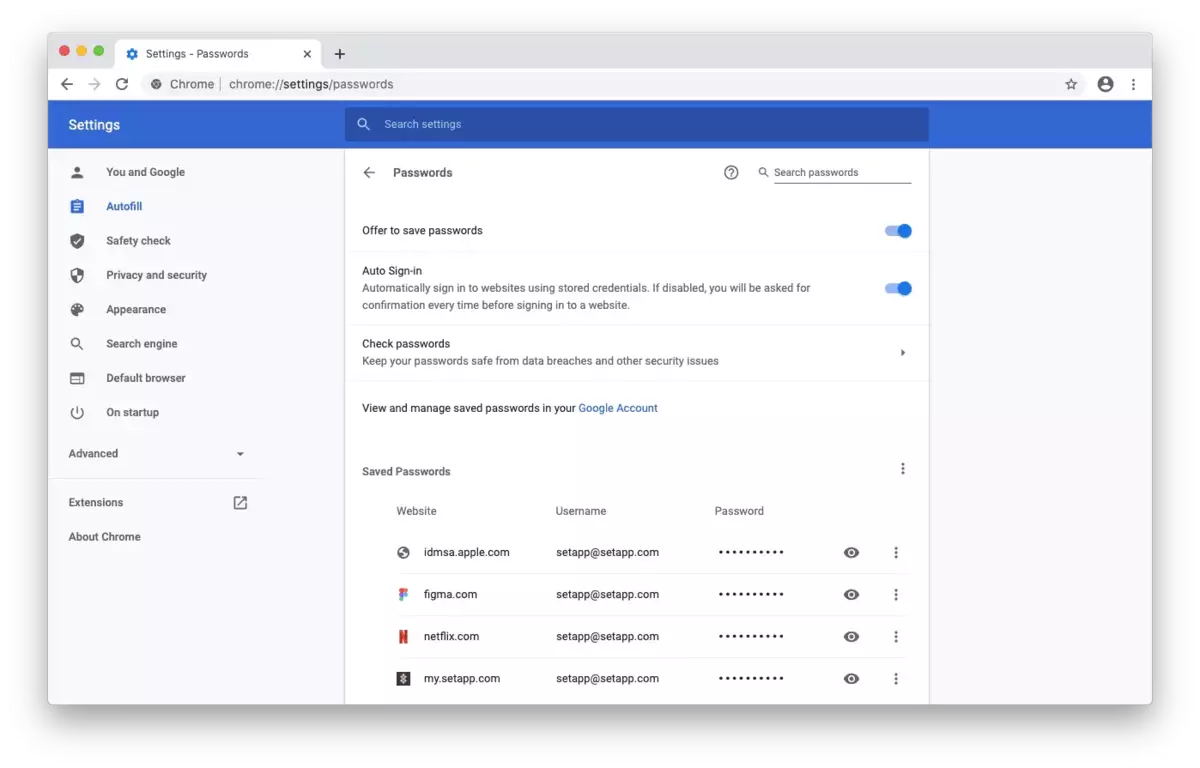
A common Internet mistake: saving your passwords in Chrome
Saving your passwords in browsers like Chrome or Opera is one of the most common Internet mistakes. Of course it’s a convenient option for the user to avoid remembering all the passwords to log in to mail, social networks or services. But keep in mind that passwords are the main objective of hackers throughout the … Read more A common Internet mistake: saving your passwords in Chrome