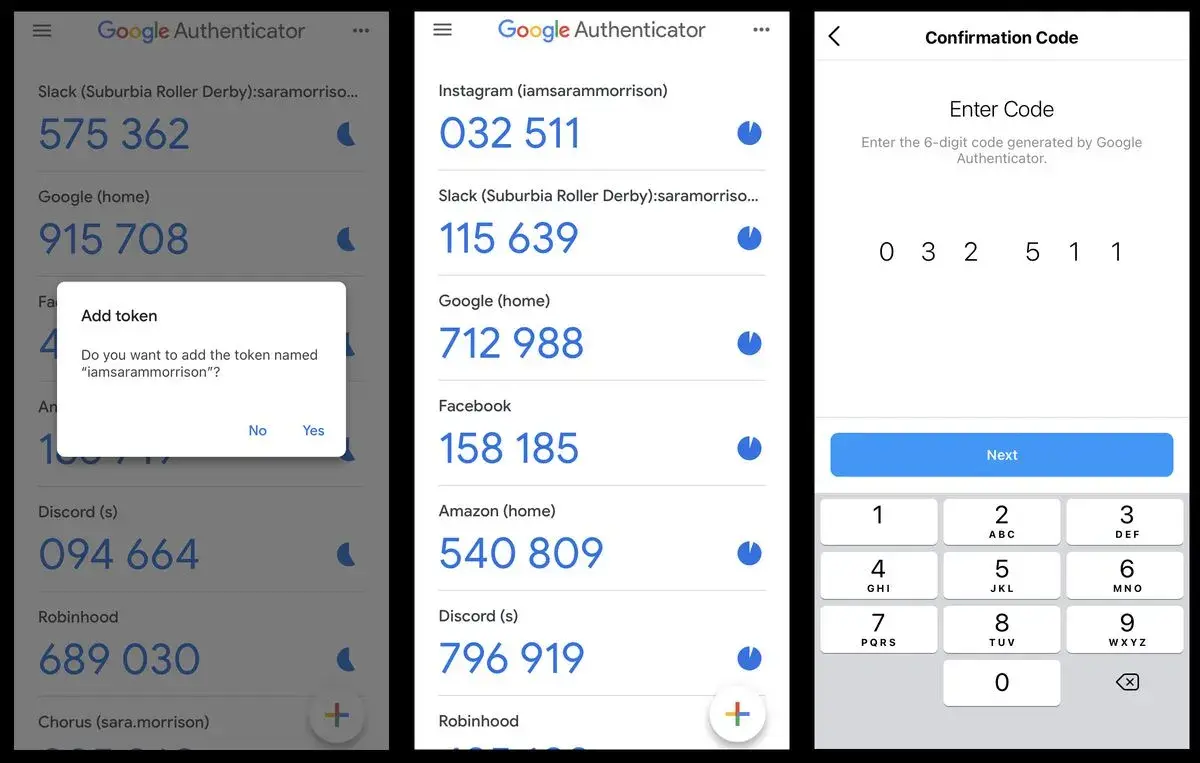
Avoid using your PIN 100 times a day with a Smartwatch
Smartwatch users usually wear it all day long. The reason to be of a Smartwatch is helping the user to complete certain tasks without the mobile phone. The watch also includes unblocking capabilities and you can use it to bypass the PIN input every time. In case you want to keep certain screen block features … Read more Avoid using your PIN 100 times a day with a Smartwatch