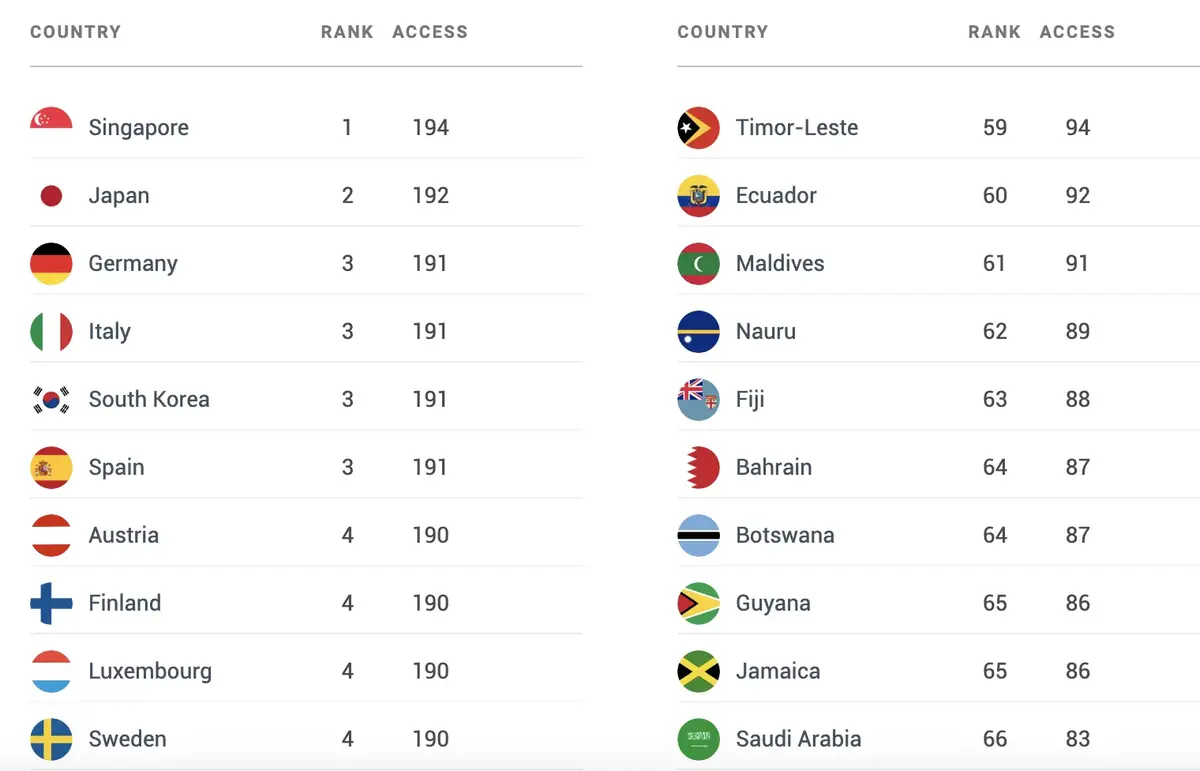
Which passports open more doors for you with the Henley Passport Index
If you want to learn about geography and curiosities all around the world, you need to check the Henley Passport Index web. It includes 199 countries all around the world and 227 destinies and the information is from 20 years back until today. It’s a website that uses data from the International Air Transport Association … Read more Which passports open more doors for you with the Henley Passport Index